The vulnerability
On May 30th researchers revealed a zero-day vulnerability in Microsoft Office that if exploited by using a malicious word document, might enable code execution on a victim’s machine.
The vulnerability, now dubbed “follina” sees a word document using a remote template feature to retrieve an HTML File from a remote server, and by using an ms-msdt MSProtocol URI scheme can execute a PowerShell.
Which versions are vulnerable?
Office 2013, 2016, 2019, 2021, and some versions of Office included with a Microsoft 365 license are subject to this vulnerability on both Windows 10 and Windows 11.
What is the risk in Remote Code Execution (RCE)?
Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine.
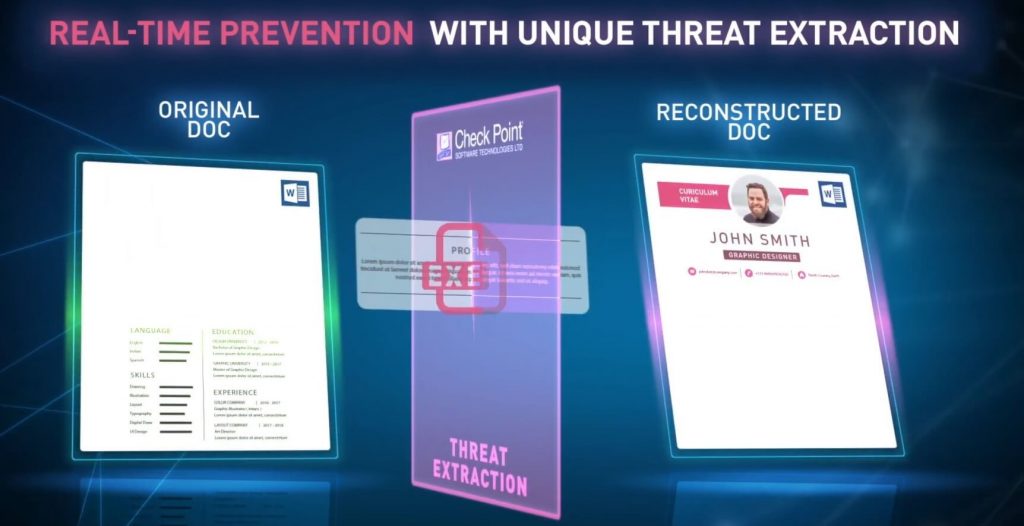
Sanitized threat free files keep Check Point customers protected
Threat Extraction delivers sanitized threat-free files to users in real-time, providing a high security posture while maintaining business flow. Email attachments and web downloads that may be affected by the new vulnerability, are sanitized on the fly, delivering safe content to users without exposing them to risks that may lurk in the original file. The original files are sent in parallel to the Threat Emulation sandbox and can easily be retrieved by the user – if they aren’t malicious.
In practice, every file received via email or downloaded by a user through a web browser is sent to the Threat Emulation sandbox to inspect for malware and malicious elements. Files are sanitized using the Threat Extraction process (Content Disarm & Reconstruction technology) to deliver sanitized content in milliseconds.
These capabilities protect Check Point customers while they are using their Endpoint by Harmony Endpoint, while browsing the internet by Harmony Browse, it’s available through our Network protection with Quantum™ Network Security, while using email accounts by using Cloud Email & Collaboration Suite Security, and on Mobile Devices, by Harmony Mobile.
On June 1st Check Point released New IPS Protections: Protection ‘Microsoft Support Diagnostic Tool Remote Code Execution (CVE-2022-30190)’ covers the vulnerability known as ‘Follina’
Watch: Check Point Harmony Endpoint vs. Microsoft Office “Follina” Exploit:
The Threat Emulation abilities are enriched with threat intelligence directly fed from Check Point ThreatCloud, the world’s largest threat intelligence resource for all IT surfaces – cloud, network, endpoints, and mobile devices.
Best Practice Recommendations:
Check Point urges users to practice the following on regular basis:
1. Never open document from that you don’t expect , even if it comes from known senders.
2. Unless there is clear need, don’t turn off protected mode from documents that originate from internet or email.
3. Refrain from opening .rtf files that originate from internet, even in preview mode.
Microsoft has released protection guidance and assigned CVE-2022-30190 to this vulnerability.
Check Point researchers closely monitors this evolving story and will continue to report as more information becomes available.
About Check Point Software Technologies Ltd.
Check Point Software Technologies Ltd. is a leading provider of cyber security solutions to corporate enterprises and governments globally. Check Point Infinity´s portfolio of solutions protects enterprises and public organizations from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware, and other threats. Infinity comprises three core pillars delivering uncompromised security and generation V threat prevention across enterprise environments: Check Point Harmony, for remote users; Check Point CloudGuard, to automatically secure clouds; and Check Point Quantum, to protect network perimeters and datacenters, all controlled by the industry’s most comprehensive, intuitive unified security management. Check Point protects over 100,000 organizations of all sizes.
*Disclamier: "The pages slugged ‘Press Release’ are equivalent to advertisements and are not written and produced by Industry Outreach Magazine journalists/Editorial." We do not hold any copyrights towards the content or image. Image source: Newswire







