Check Point is proud to be named a Fast Mover in GigaOm’s Radar for SSA, in recognition of the speed at which Harmony Connect SASE is expected to become a Leader in this space.
Why Check Point was named a Fast Mover and Challenger
As a Fast Mover, GigaOm expects us to quickly become a leader in this space. Unsurprising, given that Check Point Harmony Connect SASE takes the same technology trusted by national banks and governments for almost three decades, and makes it easy to deploy, manage and use for everyone.
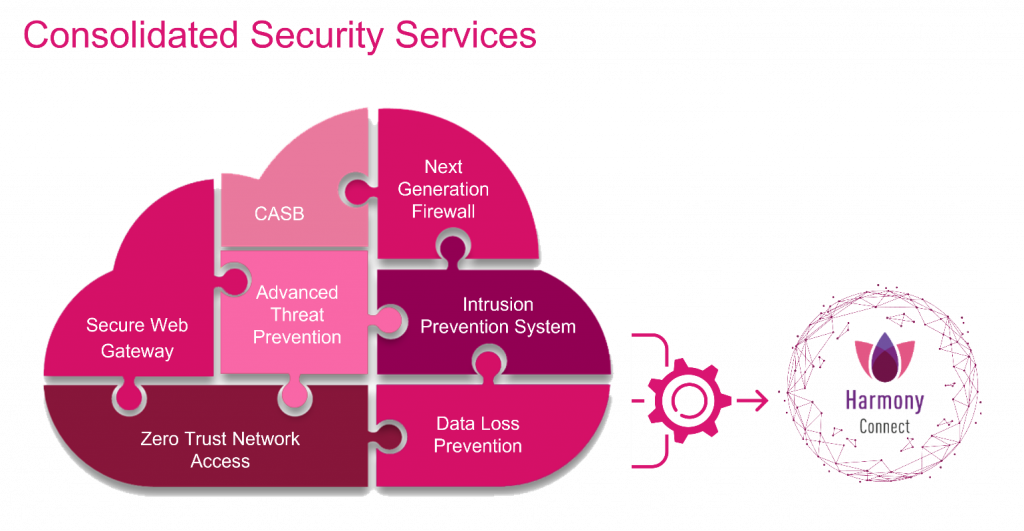
Harmony Connect SASE it delivers ZTNA, SWG, CASB, and FWaaS to protect users and branch offices with zero-trust access control, advanced threat prevention and data protection—and all with a highly intuitive UI that customers love and security effectiveness that affords peace of mind.
Harmony Connect is part of Check Point’s cloud-based Infinity architecture, delivering consolidated security for your network, cloud, users & access with unified management and security operations for a complete, future-proof security framework.
Secure Service Access – Ubiquitous User-centric Network Security
With each new user, cloud or datacenter added to your IT environment, security becomes more complex.
Compounding that challenge are variables such as hybrid work models, IoT, distributed branch offices and third-party users such as partners and consultants.
With so many moving parts to protect, is a consistent security policy across your digital estate even impossible?
Recognizing the eclectic nature of today’s IT environment, GigaOm has coined the term Secure Service Access (SSA) solutions, to denote the sea shift in the way network security is consumed; namely moving from datacenter or edge-centric services to security services that are ubiquitous and user centric. “Leveraging cloud-native, layered security functions, SSA meets each organization’s unique needs irrespective of network architecture, cloud infrastructure, user location, or device.”
What makes a network security solution an SSA solution?
To be included in the report, GigaOm identifies several features and capabilities that have been adopted hand over fist in light of today’s widely varied IT estates. Namely, these include:
- Cloud-native convergence of networking and security capabilities
- Location-dependent service delivery
- User-centric policy enforcement
- Distributed policy enforcement
- Standardized software-defined architecture
Specific SSA capabilities examined run the gamut of core network security services, such as ZTNA, SWG, CASB and FWaaS to additional services such as network detection and response (NDR), IoT and DNS security, among others.
Harmony Connect SASE – Simple, Prevention-focused Security
Harmony Connect stands out from the crowd in its laser-focused prevention-first approach and its exceedingly simple management interface. Both have won us the trust and loyalty of new and current customers.
Laser-focused Prevention-first Strategy
Harmony Connect is focused on preventing threats from ever entering your network, let alone reaching your users and devices. Across ransomware, phishing and malware—Harmony Connect’s network security serves as a first line of defense protecting branch offices and remote user internet access, as well as your organization’s servers and applications.
With all internet and corporate traffic routed through the Harmony Connect cloud, all traffic is thoroughly vetted across all ports and protocols, with the highest malware catch rate, a cutting-edge intrusion prevention system and advanced URL filtering that catches what everyone else misses. Case in point… Check Point’s patented technology makes it immune to SNI Fraud, with Harmony Connect the only solution among leading SSE vendors to catch this technique for bypassing URL filtering—a capability that can make the difference between a data breach and keeping safe. Harmony Connect provides the highest level of security with no compromises.
Exceptional Ease of use
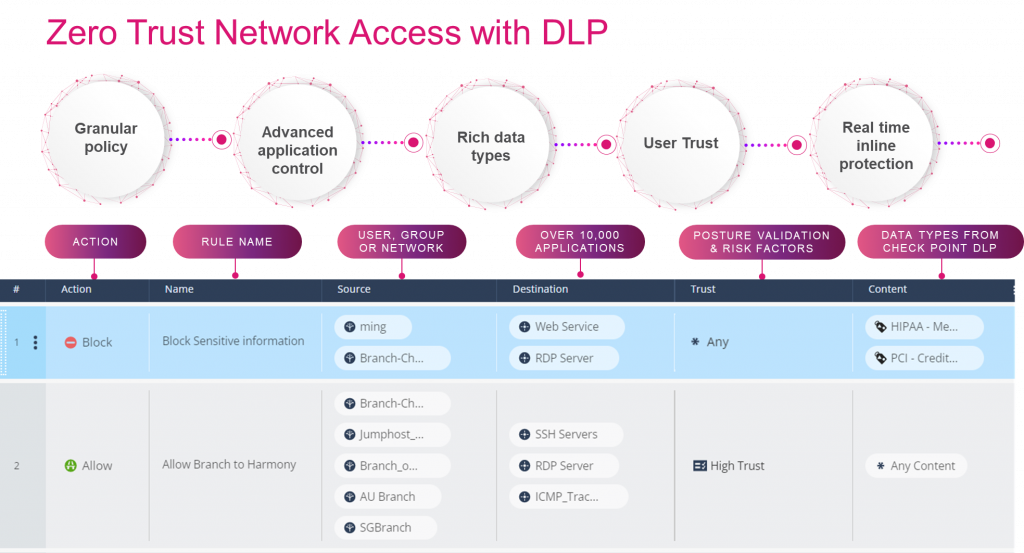
Whether its internet access or corporate access, you need only one policy to secure access and prevent data leakage. Other solutions require several different management consoles and over a dozen different policies.
*Disclamier: "The pages slugged ‘Press Release’ are equivalent to advertisements and are not written and produced by Industry Outreach Magazine journalists/Editorial." We do not hold any copyrights towards the content or image. Image source: Newswire







